NahamCon CTF 2024 - 1337 Malware
by Jstith
We received a plea for help from a rather frustrated looking employee. He said he accidently ran malware on his computer, but when he tried to pay the “leet hacker” to get his files back they said the malware was “broken”… best IT could do was provide us a PCAP.
Attachments: 1337-malware.pcapng
Solution
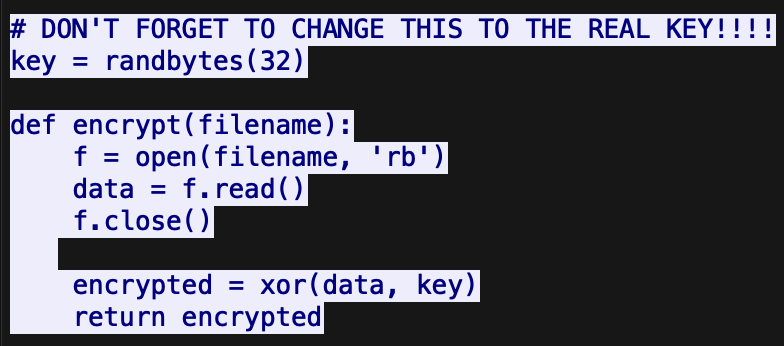
Inside the pcap, there is a python script that attempts to exfiltrate data from the victims’ machine. The program encrypts the data by XORing it using a random 32-byte value.
The cool thing about XOR is that we can easily reverse the encryption by XORing the data with the same key. The challenge here is that we don’t know the key.
Following a few of the TCP streams, it became apparent that the data being exfiltrated is clearly defined.
1
2
3
4
5
Sending: /home/davey/Documents/resources.zip
Sending: /home/davey/Documents/ecorp.png
Sending: /home/davey/Documents/Welcome Aboard.pdf
Sending: /home/davey/Documents/.ssh/id_rsa
Sending: /home/davey/Documents/.ssh/id_rsa.pub
We need to find a way to retrieve the key. Knowing a few things about XOR, the file’s bytes are XOR’d sequentially using the key in a cyclic manner. So if we know what the first 32 bytes of a file SHOULD be, we can actually XOR those encrypted bytes with the expected bytes to get our full key. Looking at the files, the easiest one to reverse has to be id_rsa.
1
-----BEGIN RSA PRIVATE KEY-----
The proess is simple:
- XOR each byte of the known plaintext with the corresponding byte of the ciphertext.
- This will reveal the 32-byte key, which is then cyclically repeated across the file.
key XOR plaintext = ciphertext <==> plaintext XOR ciphertext = key
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
import os
from random import randbytes
from pwn import xor
str = "-----BEGIN OPENSSH PRIVATE KEY--"
def encrypt(filename):
f = open(filename, 'rb')
data = f.read()
f.close()
encrypted = xor(data, str.encode())
return encrypted
key = encrypt('file.bin')[0:32]
print(key)
with open('key.bin', 'wb') as fout:
fout.write(key)
I wrote the key to a file. I then used that key to decrypt the XOR’d files, found a password in the PDF, then used that password to decrypt the ZIP.
1
flag{c95c4ff18b0eb88123de779051a7a24f}